Apple unveil dedicated password – Apple unveils dedicated password manager—a game-changer for Apple users tired of juggling logins. This isn’t just another keychain update; it’s a fully-fledged password manager designed for seamless integration with the existing Apple ecosystem. Imagine a world where password management is effortless, secure, and completely integrated with your iPhone, iPad, and Mac. This hypothetical app promises to simplify your digital life, addressing common security concerns with sophisticated encryption and user-friendly design.
From its evolution in macOS and iOS, Apple’s approach to password security has steadily improved, but a dedicated app would take it to the next level. This potential new manager would boast advanced features like biometric authentication, robust encryption, and automatic password generation, all while maintaining Apple’s high standards for user privacy. Think of the convenience: a single, secure vault for all your passwords, effortlessly synced across your devices. We delve into the potential features, security protocols, and the overall user experience this dedicated password manager could offer.
Apple’s Password Management History
Apple’s journey in password management reflects a broader industry shift towards simplifying security while bolstering its robustness. From relatively basic keychain functionality to the sophisticated iCloud Keychain we know today, Apple’s approach has consistently prioritized user experience alongside security enhancements. This evolution showcases a continuous effort to make password management less of a chore and more of a seamless, secure background process.
Early iterations of Apple’s password management were largely integrated within individual applications. Think back to the pre-iCloud Keychain days on macOS and iOS – passwords were often stored locally, within the application itself, offering minimal cross-platform synchronization or advanced security features. This approach, while functional, lacked the centralized management and security features that modern password managers offer.
Keychain’s Evolution on macOS and iOS
The introduction of Keychain Access on macOS and its iOS counterpart marked a significant step forward. Keychain provided a centralized repository for passwords, offering better organization and some basic security features like encryption. However, it primarily functioned within the confines of a single device. Synchronization between devices was limited, and features like password generation were rudimentary. Security relied heavily on the operating system’s overall security posture, leaving room for vulnerabilities if the device itself was compromised.
iCloud Keychain: Cross-Device Synchronization and Enhanced Security
The arrival of iCloud Keychain revolutionized Apple’s password management strategy. This service introduced seamless synchronization across all Apple devices, eliminating the hassle of manually entering passwords on multiple platforms. Moreover, iCloud Keychain integrated advanced security measures, including end-to-end encryption, ensuring that only the user (with their device’s passcode or biometric authentication) could access their stored passwords. Two-factor authentication further strengthened security, making it significantly harder for unauthorized individuals to gain access even if they somehow compromised a user’s Apple ID. The implementation of strong password generation and autofill features also significantly improved user convenience and security practices.
Comparison with Google and Microsoft Password Management
Apple’s iCloud Keychain competes directly with Google Password Manager and Microsoft’s password management features integrated into its ecosystem. While all three offer cross-device synchronization and password generation, key differences exist. Google Password Manager, for instance, boasts strong cross-platform compatibility, extending beyond the Apple ecosystem. Microsoft’s solution, deeply integrated with Windows and other Microsoft services, offers a similar level of cross-platform functionality. However, Apple emphasizes end-to-end encryption as a core feature of iCloud Keychain, a point of differentiation from its competitors, who might employ different encryption models or levels of user data access. The choice between these solutions often boils down to individual preferences regarding ecosystem loyalty and specific security priorities. For users deeply invested in the Apple ecosystem, iCloud Keychain’s seamless integration and strong end-to-end encryption are significant advantages. For users with a more diverse technology landscape, Google or Microsoft’s broader compatibility might be more appealing.
Features of a Dedicated Password Manager
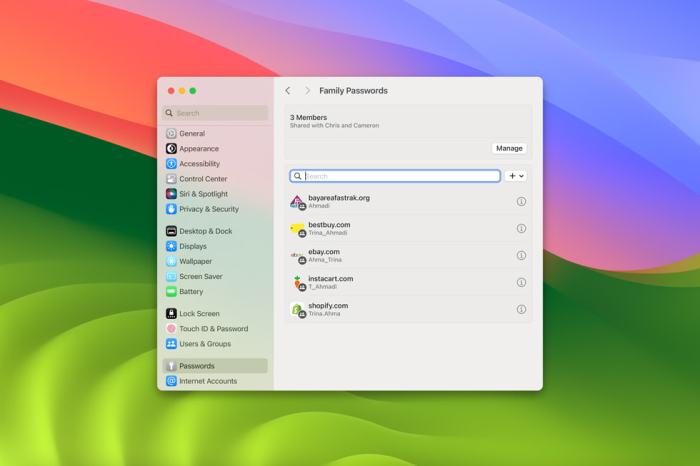
Source: apple.com
Apple’s foray into a dedicated password manager isn’t just about adding another app to its ecosystem; it’s about seamlessly integrating security into the very fabric of the Apple experience. Imagine a password manager so intuitive, so secure, and so deeply integrated, it practically disappears into the background, quietly safeguarding your digital life. This hypothetical app, let’s call it “Apple Keychain Pro,” aims to redefine password management.
This dedicated password manager would move beyond the current Keychain’s capabilities, offering a more robust and user-friendly experience. It would leverage Apple’s existing strengths in security and design, creating a solution that’s both powerful and accessible to all users, regardless of their technical expertise. We’ll explore the key features, security protocols, and user interface design that would make Apple Keychain Pro a game-changer.
Key Features of Apple Keychain Pro
Apple Keychain Pro would boast several key features designed for both simplicity and advanced functionality. These features are carefully chosen to address common pain points associated with password management while maintaining Apple’s commitment to user privacy and security.
- Biometric Authentication: Utilizing Face ID and Touch ID for seamless and secure access. No more remembering complex master passwords; your face or fingerprint is your key.
- Advanced Password Generation: The app would generate incredibly strong, unique passwords for each account, eliminating the need for users to struggle with creating secure passwords themselves. It would also offer options for customizing password length and character types.
- Cross-Device Synchronization: Seamless synchronization across all Apple devices via iCloud, ensuring password access is always available wherever the user is.
- Secure Password Sharing: A secure and auditable system for sharing passwords with trusted individuals, offering granular control over access and permissions. This would involve end-to-end encryption and verifiable audit trails.
- Security Audits and Alerts: The app would regularly scan for weak or compromised passwords, providing users with timely alerts and recommendations for improvements. It would also flag accounts with potential security risks.
- Emergency Contact Access: A feature allowing users to designate trusted individuals who can access their passwords in case of emergency, ensuring account security even in unforeseen circumstances. This would be implemented with robust authentication measures.
Security Protocols Utilized by Apple Keychain Pro
Security is paramount. Apple Keychain Pro would employ a multi-layered security approach to protect user data.
- End-to-End Encryption: All passwords and related data would be encrypted using AES-256, a widely recognized and robust encryption standard, ensuring that only the user can decrypt and access their information.
- Secure Enclave Protection: Leveraging Apple’s Secure Enclave, a dedicated hardware component, to protect cryptographic keys and sensitive data from unauthorized access, even if the device is compromised.
- Two-Factor Authentication (2FA): Implementing 2FA for an extra layer of security, requiring both a password and a secondary verification method (like a code sent to a trusted device) to access the app.
- Regular Security Updates: Consistent updates to address emerging security threats and vulnerabilities, ensuring the app remains a secure environment for password storage.
- Zero-Knowledge Architecture: Apple would not have access to the user’s passwords; they are encrypted and stored solely on the user’s devices and in iCloud using end-to-end encryption.
User Interface Design of Apple Keychain Pro
The user interface would prioritize simplicity and intuitive navigation. Accessibility features would be a core design principle.
Imagine a clean, minimalist design with a focus on clarity. The main screen would present a categorized view of stored passwords, allowing for easy searching and filtering. Password entry would be streamlined, with autofill functionality seamlessly integrated into Safari and other Apple apps. The overall aesthetic would be consistent with Apple’s design language, emphasizing elegance and ease of use. Accessibility features would include options for larger text sizes, voiceover support, and customizable color schemes, ensuring that the app is usable by everyone.
Integration with Existing Apple Ecosystem
Apple’s new dedicated password manager wouldn’t be truly revolutionary if it didn’t play nicely with the rest of your Apple devices and services. The key here is seamless integration, making password management as frictionless as possible within the familiar Apple ecosystem. This means no jarring transitions between apps, no confusing sync processes, and a consistent experience across all your iPhones, iPads, Macs, and Apple Watches.
The beauty of this integration lies in its leveraging of existing infrastructure. Think of it as a natural extension of iCloud Keychain, but supercharged with enhanced features and a more streamlined user interface. Data synchronization and backup are handled automatically through iCloud, mirroring the reliability and security Apple users already expect. This means your passwords are safely stored and accessible across all your signed-in devices, updated in real-time, and backed up regularly to Apple’s robust cloud infrastructure. Losing your phone? No problem, your passwords are safe and easily recoverable.
Password Migration from Other Managers
Moving your passwords from another password manager to Apple’s new solution is designed to be straightforward. The process is intended to be intuitive and avoid the complexities often associated with such migrations. Imagine a simple import function, perhaps initiated directly within the settings menu of the new password manager. This function would allow you to select your current password manager (LastPass, 1Password, Bitwarden, etc.) and then securely import your entire password vault. Apple will likely utilize industry-standard data formats to ensure compatibility. The system will then verify the imported data and automatically populate the new manager with your passwords. Any potential conflicts or duplicates would be clearly flagged for your review and resolution. This minimizes the risk of errors and ensures a smooth transition to the new system.
Security and Privacy Considerations
Apple’s foray into dedicated password management raises crucial questions about security and user privacy. While the convenience of a built-in solution is undeniable, a robust security architecture is paramount to ensure user trust and prevent potential data breaches. This section delves into the potential vulnerabilities, mitigation strategies, and privacy policies surrounding Apple’s proposed password manager, comparing its features with established industry players.
Potential Security Vulnerabilities and Mitigation Strategies
A dedicated password manager, however secure, faces inherent risks. For example, a sophisticated phishing attack could trick users into revealing their master password, compromising the entire system. Another vulnerability lies in potential weaknesses within the app’s code itself, which could be exploited by malicious actors. Furthermore, device compromise, either through physical access or malware, presents a significant threat.
To mitigate these risks, Apple should implement multi-factor authentication (MFA) as a mandatory security measure. This could involve requiring a secondary verification code from a trusted device or biometric authentication in addition to the master password. Regular security audits of the app’s code are essential, employing techniques like penetration testing to identify and patch vulnerabilities before they can be exploited. Finally, strong encryption both in transit and at rest is crucial, using industry-standard algorithms like AES-256. Robust endpoint security measures on user devices should also be emphasized to protect against malware and unauthorized access.
Privacy Policy and User Data Protection
Transparency and compliance with relevant regulations (like GDPR and CCPA) are crucial for building user trust. Apple’s privacy policy for its password manager must clearly Artikel what data is collected, how it’s used, and with whom it’s shared. This includes being explicit about data retention policies and procedures for user data deletion. The policy should emphasize that user passwords are never directly accessible to Apple employees or third-party services, and that encryption keys are securely managed. Independent audits of the privacy policy and data handling practices should be conducted regularly to ensure compliance and maintain user confidence.
Comparison with Existing Password Managers
The following table compares Apple’s hypothetical password manager with two leading competitors, focusing on key security features. Note that this is a hypothetical comparison based on publicly available information and industry best practices. Specific features and implementation details may vary.
| Feature | Apple Manager (Hypothetical) | Competitor A (e.g., 1Password) | Competitor B (e.g., LastPass) |
|---|---|---|---|
| End-to-End Encryption | Yes, AES-256 | Yes, AES-256 | Yes, AES-256 |
| Multi-Factor Authentication (MFA) | Yes, Required | Yes, Optional | Yes, Optional |
| Zero-Knowledge Architecture | Yes, Planned | Yes | No |
| Security Audits | Regular, Independent | Regular, Independent | Regular, Internal |
| Password Security Scoring | Yes, Integrated | Yes | Yes |
| Emergency Access | Yes, with designated contacts | Yes, with designated contacts | Yes, with designated contacts |
Marketing and User Adoption
Source: mspoweruser.com
Apple’s foray into dedicated password management presents a unique opportunity, leveraging its existing loyal user base and reputation for security. Successfully launching this new feature requires a multi-pronged marketing approach targeting diverse user segments and addressing potential market challenges head-on. The key is to emphasize simplicity, seamless integration, and the enhanced security benefits, all while acknowledging the existing competitive landscape.
Successfully marketing Apple’s dedicated password manager hinges on a clear understanding of its target audience and their needs. A robust strategy needs to consider not just the tech-savvy early adopters, but also less tech-inclined users who might be intimidated by password management complexities. This requires tailoring the message and approach for different user segments.
Marketing Materials and Messaging
A compelling tagline and concise description are crucial for initial impact. Consider taglines like “Password peace of mind, effortlessly Apple.” or “Your Apple life, securely simplified.” A short description could emphasize ease of use and seamless integration: “Effortlessly manage all your passwords within the Apple ecosystem. Secure, simple, and seamlessly integrated with your devices.” This messaging should be consistently used across all marketing channels.
User Adoption Strategy
To promote user adoption, a phased approach is recommended. Initially, focus on existing Apple users through in-app notifications, system prompts, and email campaigns highlighting the convenience and security benefits. For less tech-savvy users, consider providing easily accessible tutorials and FAQs, perhaps even short video demonstrations. Targeted advertising on Apple’s platforms and partnerships with relevant apps and services could further broaden reach. A loyalty program offering rewards for adoption could also incentivize users. For businesses, emphasizing the enhanced security and centralized management capabilities would be a key selling point.
Challenges and Solutions in a Competitive Market
The password management market is already crowded with established players. A key challenge will be differentiating Apple’s offering. Solutions include highlighting the seamless integration with the existing Apple ecosystem, emphasizing superior security and privacy features backed by Apple’s reputation, and focusing on the user-friendly interface. Another challenge is user inertia – convincing users to switch from existing solutions. This can be addressed by offering easy migration tools and emphasizing the benefits of a unified, Apple-centric password management system. Addressing potential privacy concerns head-on, through transparent communication and highlighting Apple’s strong privacy policies, is also crucial. Finally, actively engaging with user feedback and continuously improving the service will be vital for long-term success.
Illustrative Examples
Let’s dive into some real-world scenarios to see how Apple’s dedicated password manager simplifies life and boosts security. We’ll explore how it streamlines password management across various platforms and safeguards your accounts from potential breaches.
Imagine Sarah, a busy professional juggling multiple online accounts – her work email, banking portal, social media, streaming services, and online shopping accounts. Before Apple’s password manager, she used a mix of weak, easily-guessed passwords, and a notebook (yes, a physical notebook!) to keep track of them all. This was a security nightmare and incredibly inconvenient.
Simplified Password Management Across Multiple Websites and Apps
With Apple’s password manager, Sarah’s experience is transformed. When she visits a website or app for the first time, the manager prompts her to create a strong, unique password. It automatically fills in login credentials on subsequent visits, saving her time and effort. She can easily access and manage all her passwords securely within the app, eliminating the need for sticky notes or insecure practices. The app neatly organizes her passwords by category (work, personal, shopping, etc.), making it easy to find the specific credential she needs. This centralized system eliminates the frustration of forgotten passwords and the risk of using the same password across multiple accounts.
Handling Password Breaches and Compromised Credentials
Now, let’s say one of Sarah’s online accounts, her favorite online retailer, experiences a data breach. Apple’s password manager detects this breach using its extensive database of known compromised credentials. It immediately notifies Sarah, highlighting the affected account and suggesting she change her password immediately. The app even guides her through the process of generating a new, strong password and updating it across all relevant accounts, minimizing the impact of the breach. This proactive approach offers peace of mind and ensures her accounts remain protected.
Generating Strong, Unique Passwords, Apple unveil dedicated password
The app simplifies the process of generating strong passwords. When prompted to create a new password, Sarah simply taps a button, and the manager generates a complex, random password that meets industry-strength criteria – a mix of uppercase and lowercase letters, numbers, and symbols. A built-in password strength meter visually indicates the strength of the generated password or any password she manually creates. A simple bar graph, ranging from weak (red) to very strong (green), provides clear feedback. This visual cue encourages her to use only strong passwords, eliminating guessable or weak password choices. If a password falls short of the “very strong” level, the meter suggests improvements, like adding more characters or specific types of characters, until the password meets the security standards. This ensures that all her passwords are robust and difficult to crack.
Wrap-Up: Apple Unveil Dedicated Password
Source: amazonaws.com
Ultimately, Apple unveiling a dedicated password manager could redefine password security for millions. The potential for enhanced security, seamless integration, and user-friendly design makes this a compelling prospect. While challenges in a competitive market exist, Apple’s established user base and reputation for security provide a strong foundation for success. This isn’t just about managing passwords; it’s about simplifying digital life and bolstering online security in a way only Apple could achieve.
