QR Code SQL Injection: Ever scanned a QR code only to have your phone act… strangely? That seemingly innocent square could be a wolf in sheep’s clothing, harboring malicious code designed to hijack your data. This isn’t some sci-fi thriller; it’s a real and present danger lurking in the seemingly harmless world of quick response codes. We’re diving deep into the dark side of QR codes, exploring how these convenient tools can become vectors for devastating SQL injection attacks.
Imagine a QR code leading to a seemingly harmless website, but behind the scenes, it’s injecting malicious SQL commands into your database. This could lead to data breaches, account takeovers, and even financial losses. Understanding the vulnerabilities, prevention strategies, and response mechanisms is crucial in today’s digitally connected world. We’ll cover how data is encoded within QR codes, the potential vulnerabilities in applications that use them, and crucially, how to safeguard yourself and your systems.
Understanding QR Code Structure and Data Encoding
Source: researchgate.net
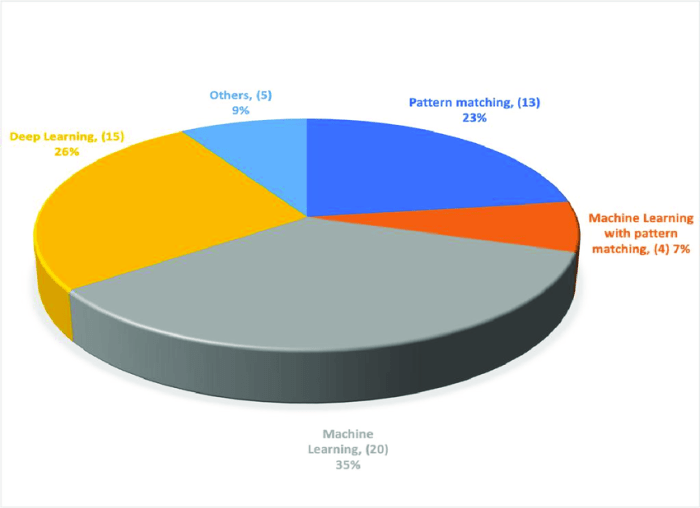
QR codes, those ubiquitous square barcodes, are far more sophisticated than they initially appear. They’re not just pretty pictures; they’re cleverly engineered to store and transmit a surprising amount of information efficiently and reliably. Understanding their structure and data encoding reveals a fascinating interplay of mathematics and visual design.
At the heart of a QR code lies a meticulously organized pattern of black and white squares. These squares aren’t randomly placed; they represent encoded data, cleverly structured to withstand damage and ensure accurate reading. The data itself is encoded using a combination of Reed-Solomon error correction and specific character sets, allowing for flexibility in the type of information stored.
Data Encoding in QR Codes
QR codes employ a sophisticated encoding system to pack data into their seemingly simple structure. The process begins by converting the input data – be it text, a URL, or other supported data types – into a stream of bits (0s and 1s). These bits are then grouped and mapped onto the code’s modules (the individual black and white squares). Different encoding modes are used to optimize the storage of various data types, maximizing the amount of information that can be packed into a given QR code size. The choice of encoding mode directly influences the efficiency of data representation. For example, using the numeric mode for a string of numbers will be far more efficient than using the alphanumeric mode.
Supported Data Types
QR codes support a variety of data types, each handled differently to optimize space and error correction. These include:
- Numeric: Digits 0-9. This mode offers the highest data density.
- Alphanumeric: Uppercase letters (A-Z), digits (0-9), and nine special characters (space, $, %, *, +, -, ., /, :).
- Byte/Binary: Raw 8-bit bytes, allowing for the encoding of virtually any data.
- Kanji: Japanese characters.
- URL: Specifically designed to encode URLs efficiently.
The choice of data type significantly impacts the amount of information a QR code can hold. For instance, a numeric-only QR code will hold significantly more data than one containing a mix of alphanumeric characters and special symbols.
QR Code Generation Process
Creating a QR code involves several steps. First, the input data is selected and its type determined. Then, the data is encoded using the most appropriate mode. Next, error correction is applied, adding redundancy to protect against damage. Finally, the encoded data is mapped onto the modules according to a predefined pattern, creating the visual representation of the QR code. This process often utilizes specialized libraries or online generators that handle the complex encoding and pattern generation automatically.
Error Correction Levels and Their Impact
The resilience of a QR code is determined by its error correction level. Higher levels mean more redundancy, leading to greater data capacity but at the cost of reduced data storage capacity. Conversely, lower levels allow for more data to be stored, but the code is less tolerant to damage.
| Error Correction Level | Data Capacity | Error Tolerance | Example Use Case |
|---|---|---|---|
| L (Low) | High | 7% | Flyers, brochures, where minor damage is unlikely |
| M (Medium) | Medium | 15% | Product packaging, marketing materials, where moderate damage is possible |
| Q (Quartile) | Low | 25% | Important documents, where significant damage is possible |
| H (High) | Very Low | 30% | Archival records, where maximum data integrity is crucial |
SQL Injection Vulnerabilities in QR Code Applications
QR codes, those handy little squares, are everywhere. But their seemingly innocent nature masks a potential security threat: SQL injection. While QR codes themselves aren’t inherently malicious, the way applications handle the data they contain can create vulnerabilities that attackers can exploit. This means that a seemingly harmless QR code could actually be a Trojan horse, leading to a serious data breach.
The vulnerability arises from how applications process the data embedded within a QR code. Many applications use user-supplied data to generate QR codes, which are then scanned and processed by another application. If these applications don’t properly sanitize or validate this user-supplied data before using it in database queries, they become susceptible to SQL injection attacks. Essentially, a malicious actor can craft a QR code containing specially formatted data that manipulates the database queries, allowing them to access, modify, or delete data they shouldn’t have access to.
Malicious Code Embedding in QR Code Data
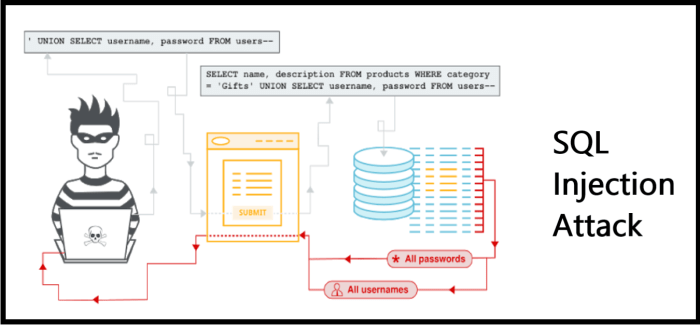
Attackers can embed malicious SQL code within the data payload of a QR code. This payload, often a URL or a string of data, can be manipulated to include SQL commands. For example, a seemingly innocent URL encoded within a QR code might actually contain something like `http://example.com/product.php?id=1;DROP TABLE users;–`. When scanned and processed by a vulnerable application, this seemingly innocuous URL could execute the SQL command `DROP TABLE users;`, effectively deleting the entire users table from the database. The `–` comments out the rest of the URL, hiding the malicious intent. The key here is that the application doesn’t properly validate or escape the `id` parameter before using it in a database query.
Exploiting Vulnerable QR Code Readers with SQL Injection
Imagine a scenario where a company uses QR codes to track inventory. Each QR code contains a product ID. A malicious actor crafts a QR code with a specially designed product ID that includes SQL injection code. When a warehouse employee scans this QR code using a vulnerable inventory management system, the injected SQL code could be executed. This could allow the attacker to access sensitive information about inventory levels, pricing, or even customer data, depending on how the database is structured and the vulnerabilities present in the application. For instance, an injected code like `’ OR ‘1’=’1` could bypass authentication checks and grant access to unauthorized data.
Risks of Using User-Supplied Data in QR Code Generation
The most significant risk stems from directly incorporating user-supplied data into the QR code without proper validation and sanitization. This creates a direct pathway for attackers to inject malicious code. A website allowing users to generate personalized QR codes with their own text input is a prime example. If the website doesn’t properly sanitize the user’s input before embedding it in the QR code, a malicious user could inject SQL code that would be executed when the QR code is scanned by a vulnerable system. The consequence could range from data breaches to complete system compromise, depending on the nature of the injected code and the security posture of the targeted system. A real-world example could be a ticketing system where users can input their own event details into a QR code, creating a potential vulnerability if input validation isn’t rigorous.
Preventing SQL Injection in QR Code Handling
So, you’ve got your snazzy QR codes, linking to all sorts of awesome stuff. But what happens when a mischievous hacker decides to inject some SQL into the mix? Suddenly, your carefully crafted database is vulnerable. Let’s dive into how to stop these digital villains in their tracks. Protecting your data is paramount, and understanding the right techniques is crucial for preventing a major headache.
Preventing SQL injection vulnerabilities when handling QR code data requires a multi-pronged approach focusing on secure coding practices and robust data validation. It’s not just about adding a layer of security; it’s about building security into the very foundation of your QR code application.
Secure Coding Practices to Prevent SQL Injection
Implementing parameterized queries is the cornerstone of preventing SQL injection. Instead of directly embedding user-supplied data into your SQL queries, you use placeholders. The database driver then safely inserts the data, treating it as data, not executable code. For example, instead of constructing a query like this:
SELECT * FROM users WHERE username = '" + username + "'
…you should use a parameterized query like this:
SELECT * FROM users WHERE username = ?
The database driver will handle the safe insertion of the `username` variable, preventing any malicious code from being executed. This simple change dramatically reduces your vulnerability to SQL injection attacks. Furthermore, always use a reputable and up-to-date database library that incorporates built-in protection against SQL injection.
Sanitizing and Validating User-Supplied Data
Before even thinking about incorporating user-supplied data into your QR codes, you *must* sanitize and validate it. This involves several crucial steps. First, input validation checks the data’s format and content against predefined rules. For instance, if you expect a numerical ID, you’d check if the input is indeed a number and within an acceptable range. Second, sanitization cleans the data by removing or escaping any potentially harmful characters. This could involve removing special characters or encoding data appropriately before using it in a database query. Think of it as a thorough security check before allowing the data anywhere near your database.
Input Validation Techniques, Qr code sql injection
Several input validation techniques exist, each with its strengths and weaknesses. Whitelisting, a stricter approach, only accepts data matching a predefined set of allowed characters or patterns. Blacklisting, on the other hand, attempts to block known harmful characters or patterns. While blacklisting might seem simpler, it’s more susceptible to bypasses as new attack vectors emerge. Whitelisting offers superior protection, ensuring only safe data is processed. Regular expressions can also play a crucial role in validating data formats, providing a powerful and flexible way to ensure that input adheres to specific patterns. However, poorly written regular expressions can themselves introduce vulnerabilities, so careful crafting is essential.
Parameterized Queries: A Practical Example
Let’s imagine a QR code containing a user ID. Instead of directly embedding this ID into an SQL query like:
SELECT * FROM products WHERE user_id = '" + qrCodeData + "'"
A parameterized query would look like this:
SELECT * FROM products WHERE user_id = ?
With the `qrCodeData` value being supplied separately as a parameter. This simple change ensures that even if `qrCodeData` contains malicious SQL code, it will be treated as plain text, rendering the injection attempt harmless. This approach applies to all database interactions triggered by QR code data.
Real-World Examples and Case Studies: Qr Code Sql Injection
Source: kratikal.com
QR codes, while convenient, aren’t immune to the dark side of the internet. Malicious actors have found creative ways to exploit their simplicity, turning these handy little squares into vectors for attacks. Let’s dive into some real-world examples of how QR code vulnerabilities have been leveraged for nefarious purposes.
It’s not just about theoretical possibilities; real-world incidents demonstrate the tangible risks associated with poorly secured QR code implementations. Understanding these cases helps us build more robust security measures.
Vulnerable QR Code Applications and Consequences
Several applications utilizing QR codes have fallen victim to SQL injection attacks. Imagine a scenario where a seemingly innocuous QR code, perhaps advertising a discount at a local store, actually redirects users to a malicious website designed to steal their login credentials or personal information. This isn’t science fiction; it’s a very real threat. The consequences can range from minor inconvenience to significant financial loss and identity theft. Compromised systems might leak sensitive customer data, leading to regulatory fines and reputational damage for the affected business.
Security Measures to Prevent QR Code Attacks
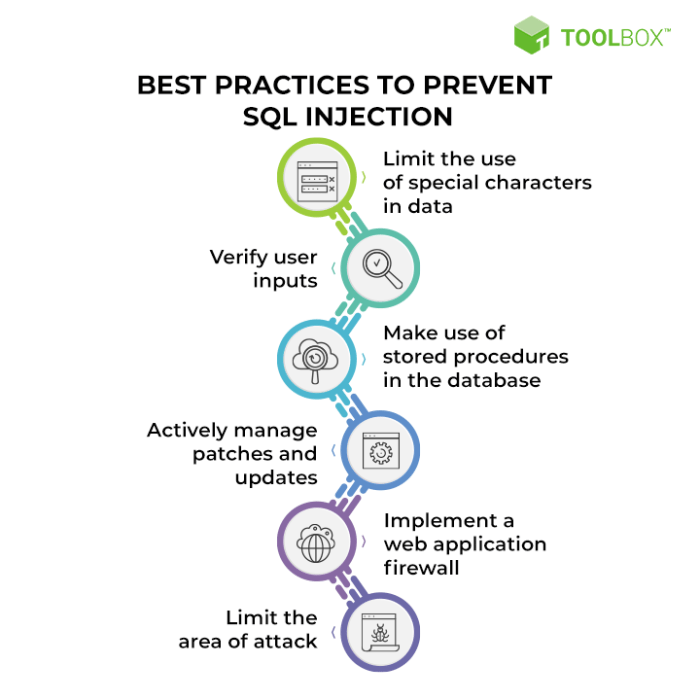
Preventing malicious QR code exploitation requires a multi-faceted approach. Robust security measures are crucial to mitigating the risks.
- Input Validation and Sanitization: Always validate and sanitize any data received from QR codes before using it in database queries. This prevents malicious code from being injected into the SQL statements.
- Parameterized Queries: Use parameterized queries or prepared statements instead of directly embedding user-supplied data into SQL queries. This isolates the data from the SQL code, preventing injection attacks.
- Regular Security Audits: Conduct regular security audits of QR code-based applications to identify and address vulnerabilities before attackers can exploit them.
- Secure Coding Practices: Follow secure coding practices throughout the development lifecycle to minimize the risk of introducing vulnerabilities.
- User Education: Educate users about the potential risks associated with scanning unfamiliar QR codes. Encourage them to be cautious and verify the authenticity of the source before scanning.
- HTTPS Encryption: Ensure all data transmitted through QR code-linked applications is encrypted using HTTPS to protect against eavesdropping and man-in-the-middle attacks.
- Strong Authentication and Authorization: Implement strong authentication and authorization mechanisms to protect sensitive data and restrict access to authorized users only.
Hypothetical Scenario: Data Theft via Malicious QR Code
Imagine a popular coffee shop uses QR codes on its tables for customers to order and pay. A malicious actor replaces one of these QR codes with their own, subtly altering the visual appearance. When a customer scans this compromised QR code, they are redirected to a fake ordering website that looks identical to the real one. This fake website harvests the customer’s credit card details and other personal information, leading to financial losses and potential identity theft. The attacker might even use the stolen data to gain access to other accounts linked to the victim’s email address or phone number. The entire process is seamless and undetectable to the unsuspecting customer, highlighting the importance of robust security measures.
Secure QR Code Generation and Scanning Practices
Source: spiceworks.com
Building secure QR code systems isn’t just about pretty visuals; it’s about protecting your data and your users. A poorly designed QR code system can be a gaping security hole, inviting all sorts of digital mischief. Let’s dive into the best practices for generating and scanning QR codes safely, focusing on preventing those sneaky SQL injection attacks.
A secure QR code generation system starts with careful data handling. Never directly embed user-supplied data into the QR code without thorough sanitization and validation. Think of it like this: you wouldn’t let a stranger walk into your house without checking their ID first, right? The same principle applies to data entering your QR code system.
Secure QR Code Generation System Design
To prevent SQL injection, the process of generating QR codes must be meticulously designed. The key is to treat all user input as potentially malicious. Before encoding any data into a QR code, it must undergo a rigorous validation and sanitization process. This involves checking for unexpected characters, data types, and lengths, and escaping any special characters that could be interpreted as SQL commands. Consider using parameterized queries or prepared statements when interacting with databases. This approach separates data from SQL code, preventing malicious code from being executed. Finally, use a robust, well-tested QR code generation library to ensure data is encoded correctly and efficiently. Never roll your own QR code generation solution unless you’re a cryptography expert with years of experience.
Secure QR Code Scanning and Processing
Securely scanning and processing QR code data involves several critical steps. First, ensure the scanning app is reputable and regularly updated, minimizing vulnerabilities. After scanning, the extracted data should never be directly used in database queries. Instead, a strict validation process should occur. This process mirrors the generation-side validation, ensuring data conforms to expected formats and lengths, and removing any potentially harmful characters. Only after this validation should the data be used to interact with databases, always through parameterized queries or prepared statements to mitigate SQL injection risks. Finally, any sensitive information obtained should be handled according to best security practices, such as encryption during storage and transmission.
Importance of Reputable QR Code Generation Libraries and Tools
Using established and well-maintained libraries and tools is paramount. These libraries often incorporate security best practices, minimizing the risk of vulnerabilities. They frequently undergo rigorous testing and updates, patching security flaws quickly. Using a reputable library significantly reduces the burden on developers, allowing them to focus on the application’s core functionality without having to become QR code security experts. Think of it as using pre-built, tested building blocks instead of trying to build everything from scratch. The risk of error and oversight is drastically reduced.
Secure QR Code Handling Process Flowchart
Imagine a flowchart. It begins with “User Input,” which flows into a “Data Validation and Sanitization” box. If the data passes validation, it moves to “QR Code Generation (using secure library)” and then to “QR Code Display/Printing.” If the data fails validation, it goes to an “Error Handling” box. On the scanning side, the process begins with “QR Code Scan,” which leads to “Data Extraction.” This then flows into “Data Validation and Sanitization,” mirroring the generation side. If the data passes, it goes to “Database Interaction (using parameterized queries),” and finally to “Application Logic.” If validation fails, it proceeds to “Error Handling.” Both sides ultimately connect to a final “Secure Data Storage” box. This visual representation emphasizes the importance of validation at both the generation and processing stages.
Mitigation and Response Strategies
So, you’ve learned about the sneaky ways SQL injection can hide in QR codes. Now, let’s talk about how to stop these digital ninjas before they wreak havoc on your database. Prevention is key, but even the best defenses can be breached. Having a solid plan for detection and response is crucial to minimizing damage and maintaining user trust.
Effective mitigation strategies go beyond simply securing the QR code generation process. It’s about building a multi-layered security approach that includes proactive monitoring, robust incident response protocols, and a commitment to regular security updates. Think of it like a fortress – multiple layers of defense working together.
Detecting and Responding to QR Code-Based SQL Injection Attacks
Detecting these attacks often relies on a combination of techniques. Intrusion Detection Systems (IDS) can be configured to monitor database activity for suspicious patterns, such as unusual SQL queries or attempts to access unauthorized data. Regular database backups are vital for recovery in case of a successful attack, allowing for a swift restoration to a known good state. Furthermore, real-time monitoring of application logs can reveal telltale signs of malicious activity, like error messages indicating SQL injection attempts. Finally, employing web application firewalls (WAFs) can help filter out malicious traffic before it even reaches your database.
The Importance of Regular Security Audits and Penetration Testing
Regular security audits and penetration testing are not just good practice; they’re essential. Think of them as a security checkup for your system. These assessments help identify vulnerabilities before malicious actors do, providing valuable insights into potential weaknesses in your QR code generation and handling processes. Penetration testing, in particular, simulates real-world attacks to uncover exploitable vulnerabilities, allowing for proactive patching and mitigation. Consider them your proactive security insurance policy. Ignoring these practices is like leaving your front door unlocked – inviting trouble.
Best Practices for Incident Response in Case of a Successful Attack
A successful SQL injection attack can be devastating. Having a well-defined incident response plan is paramount. This plan should Artikel clear steps for containing the breach, investigating the root cause, recovering affected data, and notifying affected users (if necessary). Key aspects include isolating the affected system to prevent further damage, analyzing logs to determine the extent of the compromise, and restoring data from backups. Post-incident activities should focus on patching vulnerabilities, strengthening security measures, and conducting a thorough post-mortem analysis to prevent future occurrences. Remember, swift action minimizes damage.
Steps to Take After Detecting a QR Code-Based SQL Injection Attempt
| Action | Description |
|---|---|
| Isolate the Affected System | Immediately disconnect the compromised system from the network to prevent further damage and data exfiltration. |
| Log the Event | Record all relevant details, including timestamps, user activity, and any error messages. |
| Analyze Logs and System Data | Thoroughly investigate system logs and database records to determine the extent of the compromise and identify the attacker’s actions. |
| Restore from Backup | Restore the system to a known good state using a recent backup. |
| Patch Vulnerabilities | Identify and address the underlying vulnerabilities that allowed the attack to succeed. |
| Notify Relevant Parties | Inform stakeholders, including management, security teams, and affected users (if necessary). |
| Conduct Post-Incident Review | Analyze the incident to identify areas for improvement in security practices and prevent future occurrences. |
Conclusive Thoughts
In a world increasingly reliant on QR codes for everything from accessing websites to making payments, understanding the potential for SQL injection is no longer optional—it’s essential. While the convenience of QR codes is undeniable, their vulnerability to malicious attacks highlights the urgent need for robust security measures. By implementing secure coding practices, validating user inputs rigorously, and staying vigilant against suspicious QR codes, we can mitigate the risks and navigate the digital landscape with greater confidence. Ignoring this threat is simply not an option; proactive security is the only way to stay ahead of the curve.